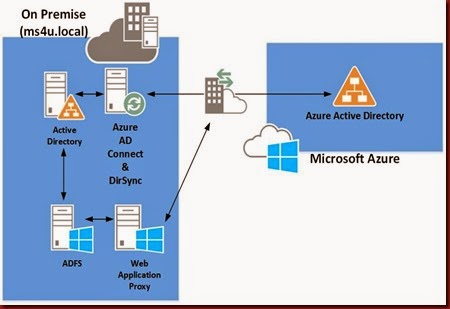
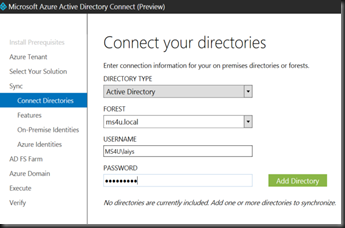
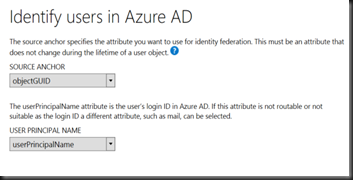
We have look on how to use AAD Connect (Azure Active Directory) to configure
However the tool is still under preview 1 and not suitable for production use. Well, in this post let look into the supported configuration on configure Active Directory Federation Services (ADFS) and Web Application Proxy for single sign-on purpose.
[Pre-requisite]
1.Create the Distribution Services KDS Root Key using Windows Powershell in Windows Server 2012 DC.
| Add-KdsRootKey –EffectiveImmediately |
Wait 10 hours or longer depend on DC replication.
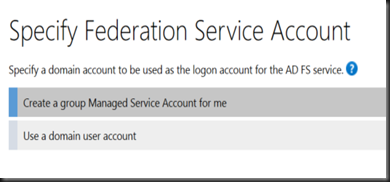
2.Create Group Manage Service Account. A security group to hold ADFS server has created. Example:- ADFSGroup.
| New-ADServiceAccount –Name MyAdminAccount –DNSHostname myAdminAccount.ms4u.local –PrincipalsAllowedToRetrieveManagedPassword “ADFSGroup” |
Command format:-
New-ADServiceAccount -name <ServiceAccountName> -DNSHostName <fqdn> -PrincipalsAllowedToRetrieveManagedPassword <group>
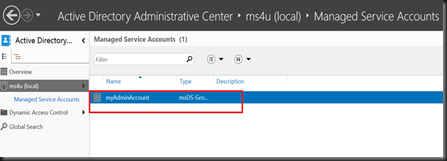
Patient and wait ! Do not configure ADFS first!!! Wait few hours till Managed Service Account appear from Active Directory Administrative Center.
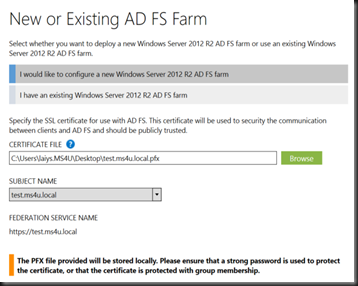
3. Install the certificate to ADFS server farm and Web Proxy. (We are using fs.ms4u.local) . You can refer to here if you want to setup for lab purpose by using Internal CA.
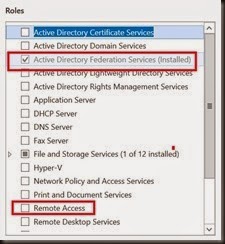
[ Add roles ]
- ADFS VM – install Active Directory Federation Services
- Web Proxy – install Web Application Proxy from Remote Access roles
- MUST separate both roles into two different VMs. Do not put ADFS and Web Proxy into the same VM.
[ Configure ADFS –1st farm ]
After install ADFS roles, next step is start the wizard from Server Manager. Follow below simple step
- Select Create 1st federation
- Select Domain Admin ID that has permission on AD
- Select public certificate that you’ve generated and installed
- Define the Group Managed Service Account that you’ve defined in earlier step
- Select database. For small scale, you can select Windows Internal Database. Meanwhile, for more than 5 servers, it is recommended to setup SQL Server





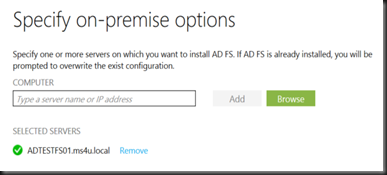
[Add 2nd ADFS Server to server farm]
On subsequent ADFS Server Farm, select Add a federation server to a existing federation server farm.
- Specify domain admin account
- Enter your primary Federation Server info
- Select the same public certificate that you’ve installed on 1st server
- Select the same Group Managed Service Account





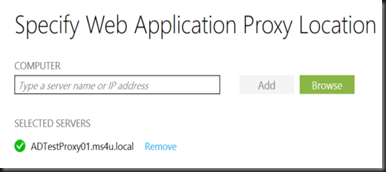
[ Configure Web Application Proxy ]
Web Application proxy provides proxy functionality for Active Directory Federation Services (ADFS) to help system administrator secure access to an ADFS.
- In the Federation service name box, enter the fully qualified domain name (FQDN) of the AD FS server; for example, fs.ms4u.local
- Define local admin right on the federation server
- Select the same public certificate used by federation server



Voila !. That’s all the configuration. Now you’ve ADFS server farm and Web Application proxy server setup in your production environment.
Hope this simple guide assist and provide you a simple step to more forward.
Good luck on your setup!